NERC has issued its 2024 Cyber Security Report, reviewing reported incidents related to Reliability Standard CIP-008-6. The details of cyber incidents provide important lessons learned that can help all utilities adapt their security and compliance programs and better protect reliability for their customers.
2024 Incidents
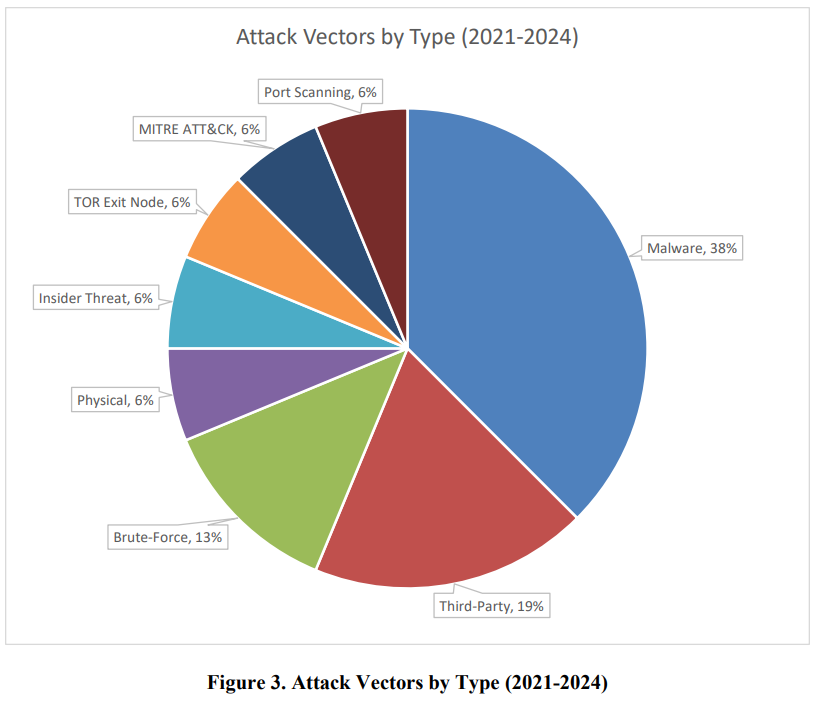
NERC recorded three CIP-008-6 cybersecurity events reported in 2024 – one in the Northeast Power Coordinating Council region, one in the Reliability First Region and one in the Western Electricity Coordinating Council region. None of these incidents compromised or functionally impacted bulk power system reliability or security. In most cases, the entity’s controls were sufficient to identify and mitigate the attacks, blocking traffic from threatening IP addresses.
The first incident was generated after a responsible entity received 20 alerts from its Security Information and Event Monitoring (SIEM) for failed login attempts to a medium impact bulk electric cyber system (BCS). This attempt to compromise tracked two IP addresses from Wyoming and Florida, both attempting to login with the same username, leading to the conclusion they were from the same attacker.
The second incident consisted of two attempts to compromise. The first was a failed brute force attack from foreign IP addresses, documented by AbuseIPDB and Talos, locking an unspecified number of user accounts and likely serving as a precursor to a second attack. Nearly a month later, was a second brute force attack, the responsible entity observed a large volume of failed authentication attempts on the same Virtual Private Network (VPN) , this time locking about 20 accounts. While not gaining the intended access to the BCS, the entity reported these attacks strained operational efficiency and IT resources needed to unlock the impacted accounts. These two attempts were attributed to the same internet service provider.
The third incident was also an attempt to compromise that occurred when a Responsible Entity observed a foreign IP address attempting to perform an active MITRE ATT&CK14 scan of its SCADA network. Based on a log review, the attacker only made initial connections to the network and then was blocked by the entity’s firewall. The attack remains under investigation to determine the source of the attack.
These three incidents are considered attempts to compromise. The number of reports from 2023 to 2024 remained the same. Two of the three 2024 attacks originated from IP addresses in foreign countries, and there was an increased level of sophistication using multiple IP addresses in two of the attempted attacks. Unlike the reports of 2022 and 2023, none of the reports mentioned involved third-party or contracted employees. However, based on recent trends, it is still important to remain vigilant regarding systems operated by both utilities and made available to contracted third parties.
Key Takeaways from Attempts to Compromise
While none of the reported events compromised the BCS or impacted reliability, NERC’s findings illustrate several important trends that should not be ignored. The threat landscape is clearly advancing, with two of the three attacks originating from multiple foreign IP addresses and demonstrating a higher level of sophistication than previous years.
Even though the attempts failed, they still carry operational consequences like locked accounts and increased pressure on IT staff, reinforcing the fact that even failed attacks can disrupt day-to-day operations and erode cyber readiness. Although the current detection and mitigation controls proved effective, the growing complexity of threats means those controls must continue to strengthen. Utilities must continue investing in stronger internal controls, staff training and real-time monitoring to stay ahead of increasingly advanced attacker capabilities and ensure their systems stay vigilant and protected.
TRC clients are encouraged to contact our security experts to assist with the development of internal controls and processes for investigating cybersecurity events. The CIP-008-6 mandatory standard has very prescriptive, time-bound reporting and compliance record keeping requirements.
Next Steps: Prepare for Incident Reporting Changes
To enhance cyber security reporting requirements, NERC is continuing its standards development project, Project 2022-05 – Modifications to CIP-008 Reporting Threshold, which resulted from efforts to assess the implementation of CIP 008-6. By establishing clearer expectations for identifying and reporting attempted compromises, the updated standard will help ensure that more consistent, timely and actionable data is shared across the industry.
The Electricity Information Sharing and Analysis Center (E-ISAC), operated by NERC, serves as a central hub for cyber and physical threat information. When responsible entities submit qualifying incidents to the E-ISAC, they contribute to a broader picture of emerging threats, helping promote industry-wide situational awareness and enabling the development of proactive security resources. Ultimately, these efforts will strengthen the collective ability of asset owners and operators to detect vulnerabilities earlier and respond more effectively, reducing risk across the bulk power system.
Resources
NERC report on 2024 Cyber Security Incidents
CIP-008-6 Reporting Threshold Standards Authorization Request
About TRC’s NERC Security Practice
TRC’s approach to power system security balances solutions that incorporate appropriate standards, regulatory requirements, best practices and operational goals and budgets. Our work for public and private sector utility clients is a testament to our understanding of NERC compliance related aspects of your business. Our successful application of technology solutions in a constantly evolving business and regulatory landscape will provide you with confidence regarding your power system compliance programs. Our power system security experts help you stay ahead of changing regulatory expectations because they stay engaged with the regulatory process and know how to plan, design and install programs that address your financial, technical and scheduling goals including compliance with changing NERC standards and guidelines as well as industry “best practices” and the latest technology developments
This regulatory update is a service to TRC’s utility clients, helping keep you informed of issues that impact your company’s compliance risks along with related topics regarding future regulatory developments to help you achieve your company’s business goals.