Cybersecurity threats to the Bulk Electric System (BES) are escalating, with attackers continuously evolving their tactics to target critical infrastructure. High-profile incidents like the Solar Wind Orion breach in 2020 have underscored the vulnerabilities of operational systems and the need for enhanced security measures. In response to notable cybersecurity risks, NERC filed two industry approved modified CIP standards on December 20, 2024, for FERC approval. These updates aim to enhance risk management by improving how critical control centers are identified and strengthening cybersecurity controls for low-impact BES Cyber Systems.
CIP-002-8 – Bulk Electric System Categorization
The proposed standard improves the risk posture of power systems by addressing the proper identification and categorization (low, medium or high impact) of Transmission Owner control centers.
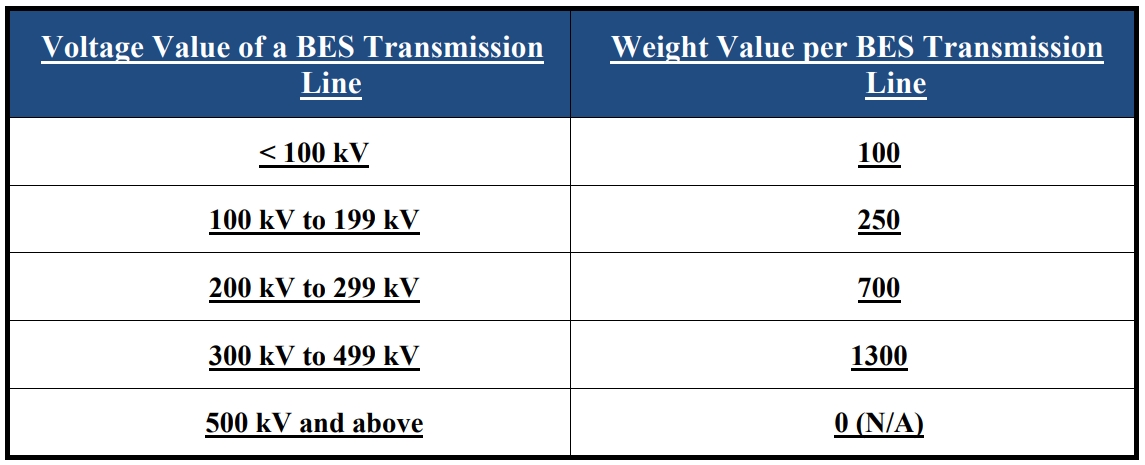
CIP-002-8 has proposed revisions to improve risk identification of newly included Transmission Owner Control Centers by applying the existing “bright-line” criteria to classify transmission assets for both Transmission Owners and Transmission Operators. Assets which if destroyed, degraded or otherwise exploited could render unacceptable impacts to the BES are scored relative to the following table to provide a weighted point value based upon transmission voltages for each line. The value of each line is added to determine the level of protection required.
CIP-003-11– Cyber Security Management Controls
On December 13, 2020, FireEye Inc., a cybersecurity solutions and forensics firm, publicly posted details about an attack on the Orion platform developed by SolarWinds. This attack was particularly damaging because in order to function, the SolarWinds Orion platform requires broad and privileged access to the networks it manages, including both the corporate and operational networks of an entity. The breach provided the opportunity for an adversary to monitor network traffic and compromise systems, which could result in disruption of operations. The breach provided the opportunity for an adversary to monitor network traffic and compromise systems, which could have resulted in the disruption of operations.
Considering these cybersecurity events and the evolving threat landscape, NERC collaborated with stakeholders to expedite a complete review of facilities housing low impact BES Cyber Assets. While these systems may not pose significant risk individually, they can be leveraged in a coordinated cyberattack, creating a higher impact threat to the BES. As a result, NERC considered the degrees of risk presented by various facilities that house low impact BES Cyber Assets and reported on whether the low impact criteria should be modified.
The proposed modifications to CIP-003-11 Cyber Security Management Controls mitigate the risks posed by a coordinated attack and add controls to authenticate remote users, protect the authentication information in transit and detect malicious communications.
NERC’s Low Impact Criteria Review Team report recommended the following additions to the CIP standards:
- Requirement(s) for authentication of remote users before access is granted to networks containing low impact BES Cyber Systems at assets containing those systems that have external routable connectivity.
- Requirement(s) for protection of user authentication information in transit for remote access to low impact BES Cyber Systems at assets containing those systems that have external routable connectivity.
- Requirement(s) for detection of malicious communications to or between assets containing low impact BES Cyber Systems with external routable connectivity.
Next Steps
NERC has filed the proposed standards with FERC. The standards will become effective, and their respective implementation plans initiated with FERC approval. TRC clients are advised to become familiar with the standard requirements updates to inform their business planning and NERC compliance activities.
Resources
About TRC’s NERC Security Practice
TRC’s approach to power system security balances solutions that incorporate appropriate standards, regulatory requirements, best practices, and operational goals and budgets. Our work for public and private sector utility clients is a testament to our understanding of NERC compliance related aspects of your business. Our successful application of technology, operational, and physical solutions in a constantly evolving business and regulatory landscape will provide you with confidence regarding your power system compliance programs. Our power system experts help you stay ahead of changing regulatory expectations because they stay engaged with the regulatory process and know how to plan, design and install programs that address your financial, technical and scheduling goals including compliance with changing NERC standards and guidelines as well as industry “best practices” and the latest technology developments
This regulatory update is a service to TRC’s utility clients, helping keep you informed of issues that impact your company’s electric compliance risks along with related topics regarding future regulatory developments to help you achieve your company’s business goals.