At its open meeting on June 26, 2025, the Federal Energy Regulatory Commission (FERC) issued Order No. 907, approving Reliability Standard CIP-015-1 – Cyber Security – Internal Network Security Monitoring (INSM). This new standard focuses on enhancing the cybersecurity of the Bulk Electric System by requiring INSM of east-west network traffic within “trust zones” specifically, the Critical Infrastructure Protection (CIP) networked environment, which includes and extends beyond the electronic security perimeter (ESP). The rule establishes a September 2, 2025 effective date which will initiate the implementation plan for the new standard.
Key Determinations and Clarifications
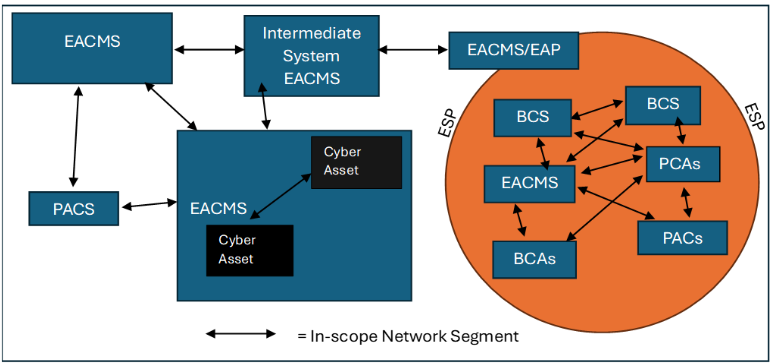
FERC approved CIP-015-1, finding it largely responsive to directives previously issued in Order No. 887 and aligned with efforts to strengthen grid security. However, FERC also directed the North American Electric Reliability Corporation (NERC) to revise the standard within 12 months to extend INSM requirements to include electronic access control or monitoring systems (EACMS) and physical access control systems (PACS). This extension applies to systems located outside the ESP.
FERC also clarified the term CIP-networked environment as used in CIP-015-1 to include
- Traffic within the ESP
- Systems within the ESP
- Network connections among and between EACMS and PACS—even if located outside the ESP
Rational for Including EACMS and PACS
FERC agreed with stakeholder commenters that incorporating EACMS and PACS into INSM provides significant reliability benefits. These systems can serve as attack vectors if compromised from outside the trust zone. Once compromised, they may introduce trusted communications into the ESP, thereby bypassing traditional security measures.
To mitigate this risk, FERC directed that EACMS and PACS be included in the CIP-networked environment and monitored accordingly.
Implementation Plan
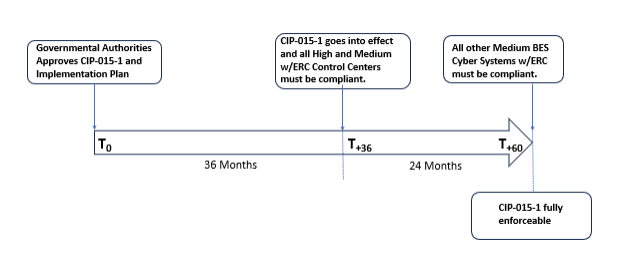
The start date for implementation (T0) for CIP-015-1 is September 2, 2025. All Responsible Entities as defined in the applicability section of the standard must begin compliance based on system type and location as follows:
- For applicable systems located at Control Centers and backup Control Centers (as identified under CIP-002-5.1(a), Requirement R1, Parts 1.1 and 1.2), full compliance with CIP-015-1 is required by T + 36 months.
- All other applicable systems must achieve compliance by T + 60 months.
Related Services
Next Steps
FERC’s approval of CIP-015-1 marks a transformative step in the evolution of the NERC CIP framework by embedding internal network monitoring alongside perimeter defenses.
TRC recommends that utility clients begin updating their cybersecurity policies, protocols, and procedures in line with CIP-015-1 and the established implementation plan. Reviewing Order 907 in detail.
Resources

About TRC’s NERC Security Practice
TRC’s approach to power system security balances solutions that incorporate appropriate standards, regulatory requirements, best practices and operational goals and budgets. Our work for public and private sector utility clients is a testament to our understanding of NERC compliance related aspects of your business. Our successful application of technology solutions in a constantly evolving business and regulatory landscape will provide you with confidence regarding your power system compliance programs. Our power system security experts help you stay ahead of changing regulatory expectations because they stay engaged with the regulatory process and know how to plan, design and install programs that address your financial, technical and scheduling goals including compliance with changing NERC standards and guidelines as well as industry “best practices” and the latest technology developments.
This regulatory update is a service to TRC’s utility clients, helping keep you informed of issues that increase your company’s electric compliance risks along with related topics regarding future regulatory developments to help you achieve your company’s business goals.